We can't find the internet
Attempting to reconnect
Something went wrong!
Hang in there while we get back on track
Mon, May 06, 2024
Platform update May 2024

Working with our customers and collecting feedback has taught us a lot when it comes to providing support and product improvements. We're working hard to incorporate all the changes requested by our customers back into our product. The list below are some improvements we've been working on and / or have already incorporated into our product.
Load Balancer Support
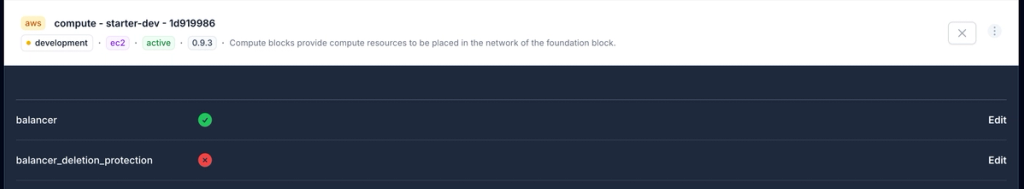
We've recently added support for load balancers to our Ops engine. This change means that we now support routing utility and web traffic over load balancers provided by the infrastructure provider.
We've smoothed out all the interactions between our ops engine and the load balancer as well. The entire setup is now load balancer aware. This means when OpsMaru interacts with your cluster / platform it will correctly connect via the load balancer provisioned by the module.
To use the load balancer simply enable in the AWS module. We are now working towards making the balancer option available in the digital ocean module as well.
AWS Module 0.9.3
We've made major progress on our AWS integration. We've incorporated new AWS components into our AWS module.
- Network Load Balancer
- Global Accelerator
- Secrets Manager
- ElastiCache Redis
- AWS Systems Manager
While some of these modules have not yet made their way into our platform, they are already available in our AWS module. We're now working towards making these modules seamlessly integrated into our platform. If you use our infrastructure builder you will already see the Network Load balancer and Global accelerator, SSM available in the compute block. These are generally available to be used today.
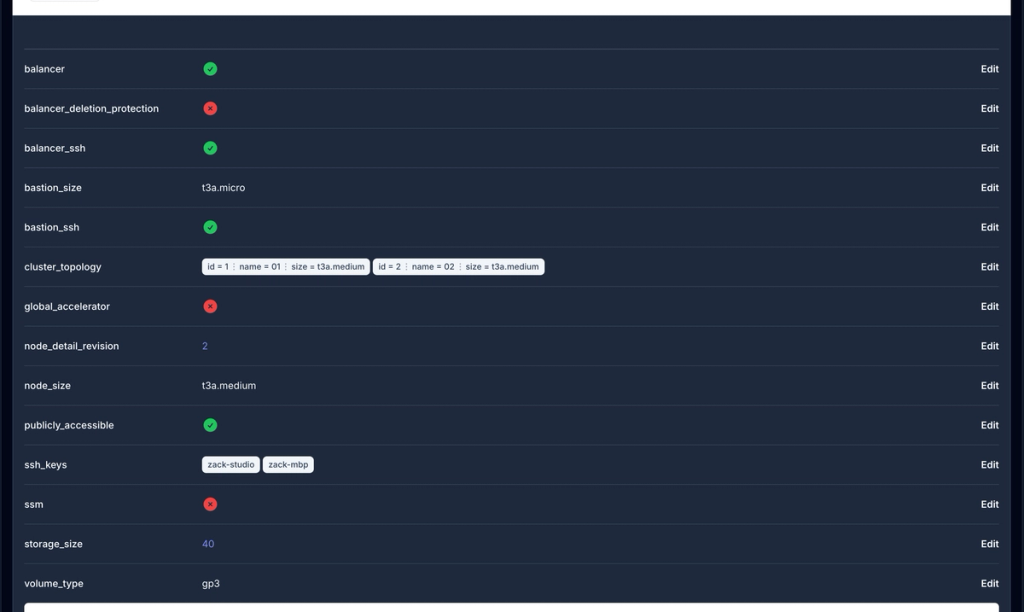
You can use the global accelerator individually or in tandem with the load balancer. The module automatically configures based on your preferences. On top of the new features in our module we've also made some quality of life improvements like enabling a single click to disable all public ports. Generally public ports are only required at cluster setup. Once you provision your cluster with a load balancer you can completely disable public port and hide your cluster from the internet. This helps improve the security profile of your cluster.
Auditable Infrastructure
We've also made it extremely easy to create an auditable cluster by integrating with AWS System Manager. What this does is it enables the nodes in your cluster to connect with SSM and provide audit information like Sofware Bill of materials and enable AWS inspector to do security scanning and provide reports to your auditor. This means clusters provisioned by OpsMaru can help fast track you towards compliance with the framework you choose.
Zero Trust Out of the Box
Another major security effort we're bringing to clusters provisioned by OpsMaru is the support for Zero Trust. We're starting with integrating with cloudflare's zero trust service. You can now get access to try out our cloudflare module and integrate it with your cluster. We have an example of how to use this module here.
Once you deploy this module in your infrastructure repository, it will automatically setup cloudflare tunnel on your bastion. This makes it easy to get up and running with zero trust for your infrastructure.
Our work doesn't stop here, we're now currently working towards integrating this module into our Code Engine to make it even simpler to use. With a single click you will be able to add this module to your infrastructure. With this integration you will also be able to disable ssh port on your bastion, making your infrastructure completely invisible to the internet.
DNS-01 Challenge Support
One of the core automations we do for our customers is SSL provisioning. We leverage caddy to provide in-cluster load balancing and routing traffic to containers in the cluster. By default caddy supports HTTP-01 challenge which means when you route a domain name to the routing node SSL is automatically provisioned. There is however one problem with HTTP-01 challenge. That is if you want to use cloudflare's orange cloud proxy HTTP-01 challenge doesn't work. We've solved this by building DNS-01 challenge support into our caddy build. You can now enable this by adding a variable called CLOUDFLARE_DNS_TOKEN to your uplink installation. You will need to setup cloudflare token with the right permissions. We will provide a tutorial on how to do this in our documentation page soon.
Conclusion
We're always happy to listen to our customer feedback. I believe this also speaks to how flexible our platform is to be able to accept customizations requested by our customers as product features. If you are looking to setup a secure, production ready, audit ready deployment platform let us know. We're always happy to help.
